Commonly known as the HIPAA regulations, the Health Insurance Portability and Accountability Act (HIPAA) of 1996 establishes guidelines for the permissible use and disclosure of patient health information (PHI).
By following a complex set of interlocking regulations, health care institutions can ensure the confidentiality, integrity, and availability of patient health information by adhering to HIPAA compliance.
What are the HIPAA Guidelines?
Several HIPAA Rules form the basis of HIPAA regulation. All of the HIPAA Rules were passed during the 20+ years since the initial HIPAA regulations were issued in 1996.
Healthcare providers should be aware of HIPAA's standards, which include:
HIPAA Privacy Rule: The HIPAA Privacy Rule establishes national criteria for patients' rights to their protected health information (PHI). The HIPAA Privacy Rule only applies to covered corporations and not to business associates. Some of the requirements specified by the HIPAA Privacy Rule involve: patients’ rights to access PHI, healthcare professionals’ rights to refuse access to PHI, the features of Use and Disclosure HIPAA release forms and Notices of Privacy Policies, and more. Documentation of HIPAA regulations should be included in the organization's policies and procedures. All staff must be educated on these policies and procedures every year, with a written certification.
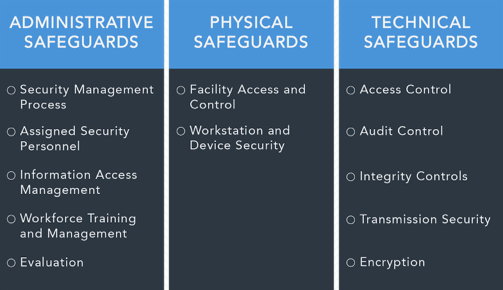
Security Rule of HIPAA: The HIPAA Security Rule establishes national requirements for the secure storage, transfer, and handling of electronic protected health information (ePHI). Because of the possibility of exchanging ePHI, the HIPAA Security Rule is applicable to both covered businesses and business associates. The Security Rule highlights specifications for the safety and reliability of ePHI, including physical, managerial, and technical security measures that must be in position in any healthcare facility. It is imperative that the organization's HIPAA Policies and Procedures document the specifics of the regulations in question. Annual training and certification of knowledge of these Policies and Procedures is required for all employees.
HIPAA Breach Notification Rule: This is a collection of protocols that covered agencies and business associates must observe in the likelihood of a data breach containing PHI or ePHI. Depending on the extent and size of the breach, the Rule specifies varying standards for breach reporting. Regardless of the size of a breach, organizations must notify HHS OCR, but the particular methodology for doing so varies based on the type of breach that has occurred.
Omnibus Rule of HIPAA: An addendum to the HIPAA regulation, known as the HIPAA Omnibus Rule, was passed to include business associates in the scope of the HIPAA regulation. The HIPAA Omnibus Rule stipulates that business associates must be HIPAA-compliant and describes the guidelines governing Business Associate Agreements (BAAs). Before any PHI or ePHI can be transmitted or exchanged, an agreement called a "Business Partner Agreement" must be signed by a covered company and a business associate, or by two business associates.
What is required for HIPAA Compliance?
In order to comply with HIPAA, all covered companies and business associates must adhere to a set of national criteria that must be met.
Self-Audits: According to HIPAA regulations, organizations that are subject to the Privacy and Security Rules must carry out annual audits of their operations to identify administrative, technical, and physical flaws that jeopardize patient data. In order to remain HIPAA-compliant, a Security Risk Assessment is not enough; it is simply one of the mandatory audits for HIPAA- compliant companies.
Remediation strategies: Self-audits can help organizations and their business partners find areas of noncompliance, but remediation strategies must be put in place to close any gaps that are found. To be effective, these strategies for gap filling must be well documented and include specific deadlines.
Procedures Policies, and Employee Training: & The HIPAA Rules require all covered businesses and business associates to create policies and procedures that adhere to the HIPAA regulatory standards. As the company grows and evolves, it is necessary to keep these rules and procedures up-to-date. Staff must be trained on these policies and procedures on a yearly basis, as well as provide written confirmation from their supervisors that they have read and understood all of the policy and procedure documents.
Documentation: The activities of HIPAA-compliant firms must be documented in full. In order to pass a HIPAA investigation with the HHS Office for Civil Rights (OCR), this documentation is essential.
Management of business partners: PHI must be documented for all suppliers with whom information is shared in any fashion by covered companies as well as business associates. In order to keep up with changes in vendor relationships, BAAs must be reviewed annually. There must be a BAA in place before any PHI is exchanged.
What are the Seven Elements of an Effective Compliance Program?
As a guide, the Office of Inspector (OIG) General for Health and Human Services (HHS) developed the Seven Elements of an Effective Compliance Program so that businesses can vet compliance solutions or even develop their personal compliance programs.
These are the core essentials of what a successful compliance program must cover. An effective HIPAA compliance program must be able to manage all seven elements of the statutory HIPAA privacy and security criteria. The following are the seven components of a successful compliance program:
Formulating written policies, practices, and standards of conduct.
Assigning a compliance officer and compliance panel.
Providing high-quality education and training.
Creating a network of mutually beneficial relationships.
Facilitating internal auditing and monitoring.
Using well-publicized disciplinary measures to enforce standards.
Punctually addressing and resolving detected violations.
Federal HIPAA auditors will evaluate your organization's compliance program against the Seven Elements during a HIPAA investigation conducted by OCR in response to a HIPAA violation.
Final thoughts
Whether a health insurance company, a data storage or server repair company, an insurance broker, or a part of any of the many other industries that touch PHI, any business that handles PHI needs to understand HIPAA and have the necessary processes and safeguards to ensure that the data is being handled safely and securely.
If you need to make sure your company is compliant, business IT support services and compliance operations software from SC Technical can make your HIPAA journey so much easier and faster. We'd be happy to have a conversation with you about how to handle your HIPAA compliance process more effectively if you're interested. All you need to do is give us a call today!



Comments